ION expands ETF trading capabilities with Tradeweb integration
Cyber stocks have been on fire this year. The rapid rise of artificial intelligence has transformed the cybersecurity landscape, amplifying both the scale of threats and the sophistication of defense mechanisms. As AI-powered attacks become more adaptive and harder to detect, cybersecurity companies have responded in kind—developing AI-driven tools that can predict, prevent, and neutralize threats in real-time. This dynamic arms race has created a thriving ecosystem for innovation and investment, positioning cybersecurity firms at the forefront of one of the most critical sectors in the digital economy.
At the heart of this evolution lies data—an asset that has grown exponentially in both volume and strategic value. However, in the world of AI, not all data is created equal. The edge increasingly lies in quality, not just quantity. Rich, contextual, and well-labeled datasets are essential for training effective AI models capable of distinguishing between benign and malicious behavior. This paradigm shift is compelling cybersecurity companies to rethink their data strategies and invest heavily in refining how they collect, clean, and utilize information.
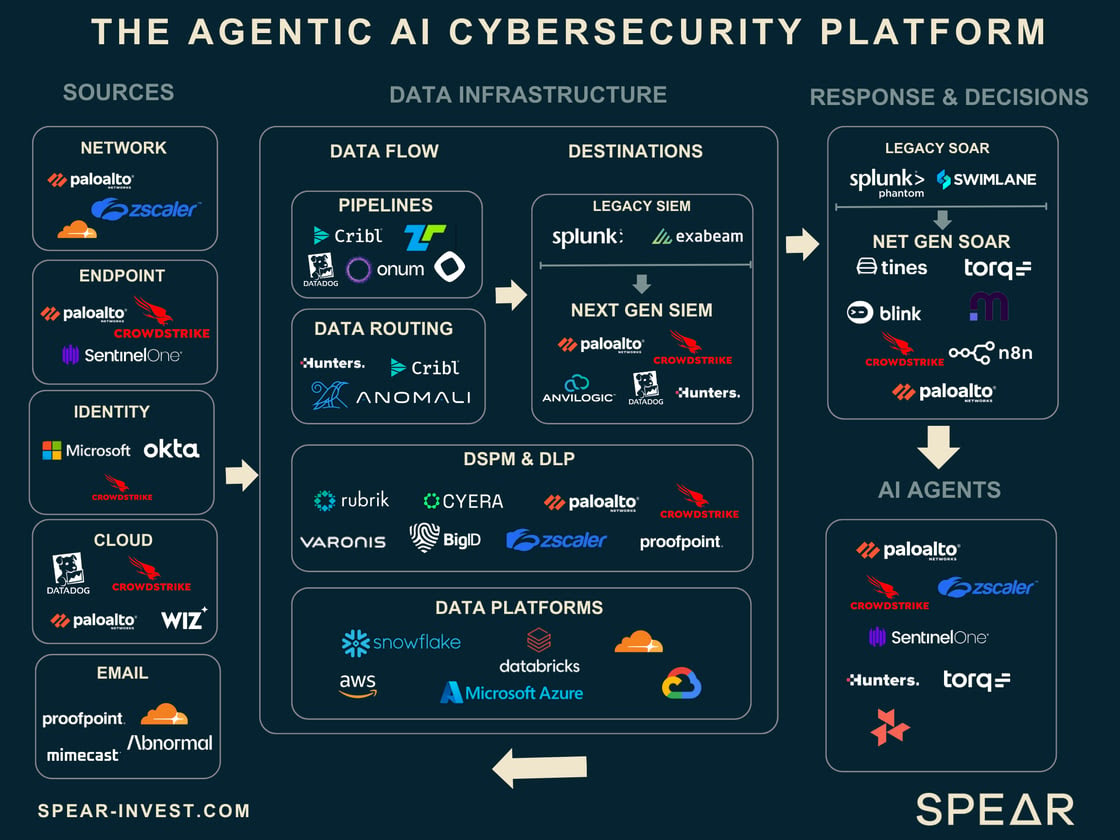 For the industry’s major players, building robust data infrastructures is no longer optional—it is foundational. As AI agents become central to cybersecurity operations, these companies must develop the pipelines, governance, and intelligence layers necessary to power them. In the next phase of cybersecurity, the winners will be those who can move from collecting data to orchestrating outcomes and build cohesive platforms.
For the industry’s major players, building robust data infrastructures is no longer optional—it is foundational. As AI agents become central to cybersecurity operations, these companies must develop the pipelines, governance, and intelligence layers necessary to power them. In the next phase of cybersecurity, the winners will be those who can move from collecting data to orchestrating outcomes and build cohesive platforms.
These developments have contributed to the rise of the modern SOC (Security Operations Center) enhanced by AI. While AI Agents are the ultimate goal, the value lies in the Data Source and the Data Infrastructure Layer.
The Modern SOC: Evolving the Nerve Center of Cyber Defense
The SOC (Security Operations Center) is the heart of cybersecurity operations. Every alert or response, from endpoint to cloud, flows through it. While SOCs have existed for decades, the role and functionality of the SOC significantly evolved over the past year+.
The modern SOC is not a dashboard with static data, but a system integrating source data into actionable insights. The data could be coming from different sources, such as the network, endpoints, identity, or the cloud. The challenge of the SOC is processing and sifting through this data, which is usually not properly labeled and in different formats.
From a public company investment perspective, we are laser-focused on figuring out how each company is positioned to capture a significant portion of this evolving market. As Palo Alto management pointed out, customers don’t want to be system integrators, implying that companies delivering a cohesive platform will win.
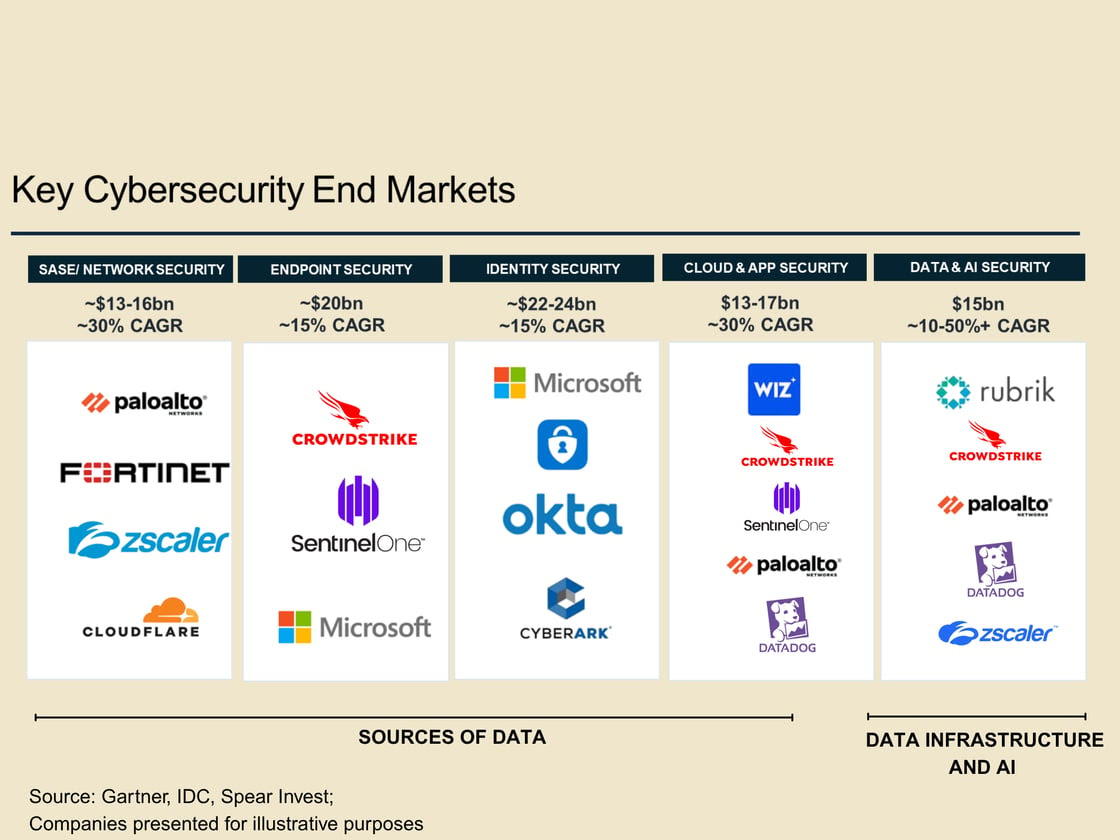
The leaders in network, endpoint, identity, cloud, and e-mail security are sitting on a vast amount of data, which puts these companies in a unique position to capture value.
Strategic Data Leverage by Cybersecurity Leaders
Here are a few examples:
- CrowdStrike Holdings Inc (NASDAQ:CRWD), a leader in Endpoint Security, processes over 5 trillion events per week, with over 150 million indicator of attack (IOA) decisions made every second; stores over 15 petabytes of data in the cloud and protects over 1 billion containers daily.
- Zscaler (NASDAQ:ZS), a leader in Network Security, processed over 100 trillion transactions, blocked over 60 billion threats, and enforced over 5 trillion policies last year alone.
However, how these companies filter, organize, and use the data will be a key differentiator in the next growth phase. Not surprisingly, most of the larger bolt-on acquisitions have been focused on the Data Infrastructure layer, building on solid positions that each company has in their respective core markets.
- Crowdstrike acquired Flow Security, a company specializing in cloud data runtime security, to enhance its DSPM offerings for ~$110 million in March ’24.
- Palo Alto Networks (NASDAQ:PANW) acquired Dig Security, a provider of Data Security Posture Management (DSPM), for $200–400 million in October ’23, IBM’s QRadar, adding SIEM capabilities for $1.14 billion in Sept. ’24, and Protect AI for ~$600–700 million, expected to close in 1Q’26.
- Zscaler acquired Avalor, a data fabric platform, for $350 million in March ’24, and recently announced the acquisition of RedCanary, a Managed Detection and Response (MDR) platform, for $675 million, expected to close in August ’25.